Service Description: Nuvolo OT Security – Inventory & Workflow and Monitoring & Response and Risk Assessment - Thailand
SKU Numbers: NUV-SERV-OTS-ALL-T and NUV-SERV-OTS-ALL-T-EM
Overview
Nuvolo’s OT Security Inventory & Workflow module is designed to keep up-to-date asset information by correlating your Connected Workplace assets with information from your real-time network monitoring solution. Combined with OT Security Monitoring & Response, keep up-to-date asset information correlated with security relevant information to help secure the fleet.
Nuvolo’s OT Security Risk Assessment module is designed to provide a framework for performing risk assessments surrounding Operation Technology, build out a risk management framework, and associate controls to mitigate risk. Due to this functionality, it is inherently designed to be configured to the needs of the individual organization.
Implementation
Activation
Nuvolo and Customer will collaborate for the activation of the Nuvolo application. This marks the start of the engagement. The activation will begin with a kickoff meeting for the teams to meet and review the implementation process.
Nuvolo will:
- Schedule remote project kickoff meeting for introductions.
- Create implementation kickoff agenda.
- Schedule and conduct implementation kickoff:
- Review project roles and responsibilities.
- Review of Customer’s organizational constraints.
- Review of project approval processes to avoid unnecessary delays.
- Agree on sprint cycle plan with Customer.
- Understand Customer’s network security requirements and approvals.
- Review Customer’s and Nuvolo’s escalation processes.
- Review Customer’s business requirements.
- Define scrum call schedule.
- Review UAT training requirements and level of effort.
- Receive list of subject matter experts (SMEs) from Customer’s business units.
Customer will provide:
- Appropriate and knowledgeable staff to complete self-paced learning at the appropriate times and participate in the implementation.
- One or more Nuvolo application administrator for each Nuvolo application as appropriate.
- Customer deliverables as identified for the implementation as scheduled.
Inventory & Workflow Installation Activities and Tasks
Nuvolo will:
- Perform the initial application installation in lower instances (Dev, Stage/Test)
Matched Assets Workflow Activities and Tasks
Nuvolo will:
- Discuss the process that will occur with incoming data from the Network Security Monitoring Solution
- Configure appropriate key/field mappings
- Configure appropriate identifications
Customer will:
- Provide sample payload information surrounding the Network Security Monitoring solution
- Decide which data elements from the payload to be used for updating asset information
- Define which data elements from the payload will be used for identification purposes
Unmatched Assets Workflow Activities and Tasks
Nuvolo will:
- Configure workflow surrounding unmatched assets
- Configure work order auto-generation
Customer will:
- Decide whether unmatched assets should create work orders for validation
- Decide whether unmatched assets should automatically create new assets
Vulnerability Data Imports
Nuvolo will:
- Import Vulnerability Definitions, CPEs, and CWEs into lower-level instances
- Enable automatic updates of Vulnerability Definitions
Security Alerts and Vulnerability Remediation
Nuvolo will:
- Discuss work orders that will be generated as part of the workflow, and configure work order generation according to customer’s decision
Customer will:
- Decide whether automatic work order generation should occur for Security Alerts and Vulnerability Remediation
Environment Cleanup and Integration Enablement
Nuvolo will:
- Remove unused network security monitoring data sources
- Remove unused network security monitoring key/field mappings
- Remove unused network security monitoring identifications
- Remove unused network security monitoring action scripts
- Provide data source sys_id for use with Network Security Monitoring integration
- Associate web only user account with data source for authorization
Customer will:
- Decide which Network Security Monitoring solution is used for integration purposes
- Create a web-only user account for use with Network Security Monitoring Solution integration
- Engage the Network Security Monitoring team for any coding that may be required on the NSM side for the integration (e.x., filter updates), and ensure it is completed within in the implementation timeline
Risk Assessment Data Preparation Activities and Tasks
Nuvolo will:
- Load (using template as defined in Data Collection and Load section) Manufacturers, Models, and associated Software and/or Firmware referential and metadata as discussed in the template walkthrough provided by the Customer.
Customer will:
- Provide Manufacturers, Models, and associated Software and/or Firmware referential and metadata [as discussed in the template walkthrough] via the template provided by Nuvolo.
Risk Assessments and Findings & Control Activities and Tasks
Nuvolo will:
- Discuss Risk Assessments, generic risk assessment types, and demonstrate how to create Risk Assessment Types for use in Model Security Lifecycle Profiles
- Discuss Findings, generic findings that would be identified and pose a risk, and how to create findings and associated risk scores to be utilized in calculating potential risk
- Discuss Controls, generic controls that could be utilized to mitigate a finding, and how to create a control/finding combination to reduce potential risk
Customer will:
- Provide relevant Risk Assessment types if applicable to their environment, these may be generic such as Initial Risk Assessment, Follow-Up Risk Assessment, or more granular, New Purchase – Unknown Risk, Repeat Purchase – Known Risk.
Work Items, Work Assignments, and Delay Activities and Tasks
Nuvolo will:
- Discuss Work Item Type definitions and configure potential work items to be completed for a given control and creation of work item types for use in risk assessments
- Discuss Work Assignments that can be used for routing work items created when addressing specific controls and demonstrate how to utilize work assignments for routing.
- Discuss potential Delays that can occur when performing a Risk Assessment and associated details and demonstrate how to create new delays that may be encountered when performing Risk Assessments.
Customer will:
- Define any work types to be configured
- Define any space assignment rules to be utilized for the specified work types
- Define any associated delays to be configured
Create Model SLPs and Device Association Activities and Tasks
Nuvolo will:
- Walk through the process of creating a Model Security Lifecycle Profile for relevant manufacturer, model, and software/firmware definitions for device association
- Walk through adding Control/Finding combinations to mitigate risk associated with relevant findings
Customer will:
- Provide a sample Manufacturer, Model, and Software/Firmware definition to be utilized for the creation of a Model SLP
Preparing Work to be Performed and Generating Work Orders
Nuvolo will:
- Walk through the process of creating tasks associated with addressing findings and implementing controls, and documenting the procedural information required to perform the steps necessary to complete the relevant tasks
- Walk through the process of generating planned work orders for devices associated with the Model SLP
- Generating the work orders to have technicians perform the procedures required to implement the controls for specified findings
Customer will:
- Provide procedural information to be used for tasks required to address Control/Finding remediation
Dashboards and Reporting Activities and Tasks
Nuvolo’s OT Security Inventory & Workflow and Monitoring & Response contains out of the box dashboards and reports to be used to gain visibility into the successful correlation of asset information between systems. Nuvolo will review out of the box reports during this engagement
Risk Assessment comes with out of the box reporting functionality, we will review the dashboards, and view the status of Model SLPs to track the work items performed for securing the fleet.
Training
Nuvolo’s OT Security Inventory & Workflow and Monitoring & Response contains multiple components to match and map assets between Nuvolo’s Connected Workplace and your Network Monitoring Solution.
- Nuvolo will review and demonstrate the following:
- An overview of the workflow and associated queues
- Identifications
- Key Field mappings
- Action Scripts
- Work Orders
- Security Events
- Device Manufacturer, Model, and Software/Firmware definition requirements
- Risk Assessment Type
- Findings
- Controls
- Risk Scoring
- Finding/Control Combination
- Work Types
- Work Assignments
- Delay Statuses
- Model SLPs
- Device Association
- Tasks
- Procedures
- Planned Work Orders
- Generating Work Orders
Change Requests
If there is a change in scope, assumptions, capability discovered during the implementation kickoff then Nuvolo will require a Change Request. Any Change Request signed by both parties shall be effective as of the date set forth therein (each, a “Change Order”). Instances in which a Change Order shall be required include: (1) Customer’s requests for out-of-scope Services; (2) discovery of new information that requires an increase in the scope of Services; or (3) Customer’s failure to fulfill any of its responsibilities if such failure delays the Services or requires Nuvolo to incur additional time or costs in performing Services.
If the parties do not agree on a Change Order, the Engagement shall proceed as originally set forth. If, however, the existing Engagement or any specific Services cannot proceed without an executed Change Order, Nuvolo may suspend Services until the Change Order is executed.
Scheduled Timeline
The duration for the setup of the services outlined in this document is up to sixteen (16) weeks.
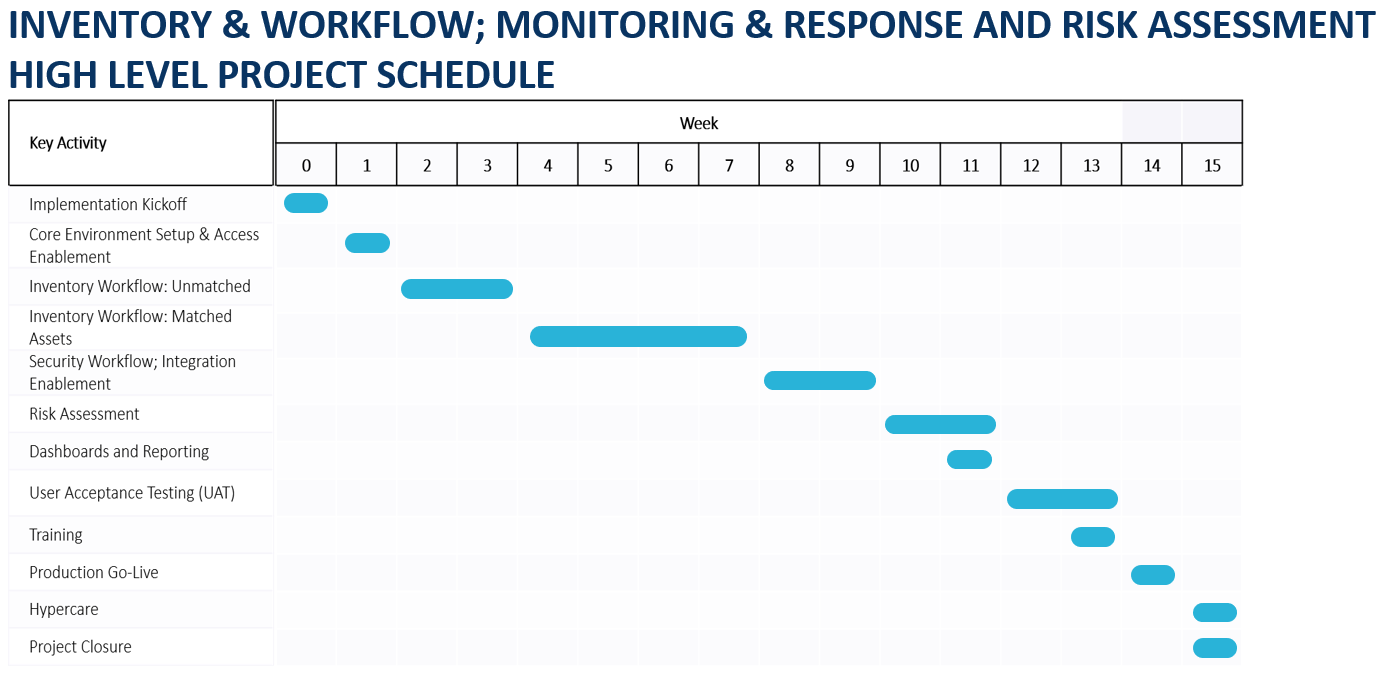
Delivery Terms
The duration of this deployment is up to sixteen (16) weeks. Any additional effort required related to complexity, scope or project duration will be subject to the change request process.
Any activities or tasks not specifically outlined in this Service Description are out of scope.
Nuvolo Access Requirements
Customer will provide access requirements and policies required of Nuvolo resources along with onboarding timelines prior to execution of this SOW. Customer acknowledges that all obligations of Nuvolo under this SOW will require Nuvolo (including any subcontractors) to have direct access to Customer’s ServiceNow sub- production instance(s). Administrative access will be required in the sub-production instance(s) only and at no time will Nuvolo have access to the production environment.
Services shall be preconditioned upon Nuvolo receiving such access and proportionately limited to the extent access is denied. Failure to provide timely access may result in timeline delays and costs increase as outlined in this SOW. Additionally, Customer acknowledges that Nuvolo will leverage a mix of onshore and offshore resources in support of the Engagement.

- Privacy Policy
- © Nuvolo 2021. All right reserved